Smart Phishing using Ticket Feature of a Customer Support Software
I found a security vulnerability in Freshdesk that enables an attacker to send ticket requests via spoofing the sender. This vulnerability can be used in real-life scenarios to create smarter phishing attempts.
The ability to easily spoof an e-mail sender is always a great risk for organizations. Attackers hiding behind a trusted sender typically try to steal credentials from the victims or hijack victims’ computers with ransomware or other malware. In order to protect against such attacks, companies need security solutions to determine whether the sender of the e-mail is real or not. In inbound email filtering solutions used by companies, they can take security measures to apply the company’s email authentication service which uses standards like SPF, DKIM, and DMARC and quarantine emails that have failed to meet those standards. With the effective implementation of such security measures, attackers develop interesting scenarios with new approaches.
Freshdesk is one of many Help Desk Softwares available for organizations to manage Customer Support Services.
Freshdesk, the online customer engagement solution from Freshworks, lets you streamline your company’s customer support using the customer service software and helps you to efficiently manage your customers as you scale.
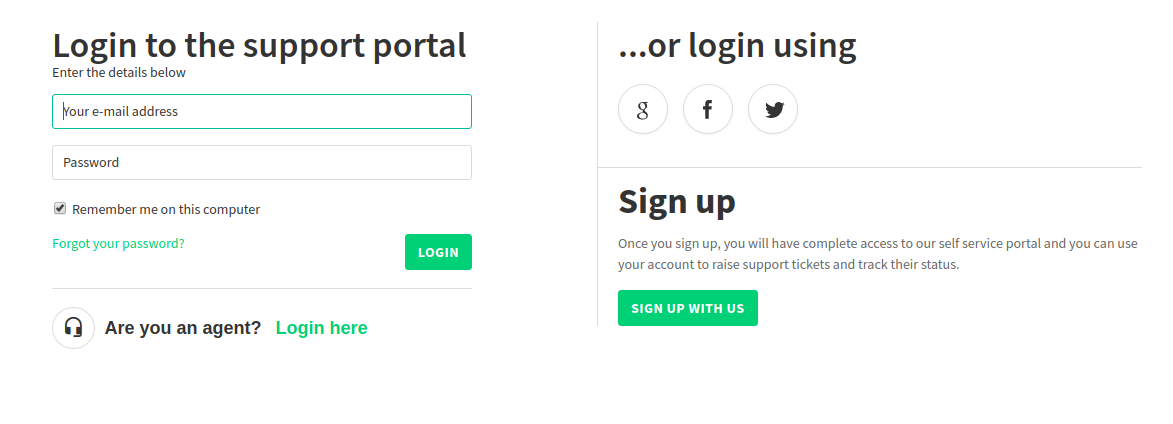
Freshdesk accounts can be accessed by default under companyname.freshdesk.com or support.company.com. When we investigate the source code of the login page, the “Login to the support portal” or “Help Desk Software by Freshdesk” information, which is the default Freshdesk title, can be descriptive information for these pages and in this way, the attackers can use the recon phase with Google dork as below.

site:*.freshdesk.com intext:“Login to the support portal” or “Help Desk Software by Freshdesk” -site:support.freshdesk.com
Due to an authorization vulnerability caused by Freshdesk, an attacker can perform social engineering attacks by impersonating trusted sources.
Support pages are not fully open to the outside. The login to the Freshdesk Support portal is as follows:
* One of these methods is used.
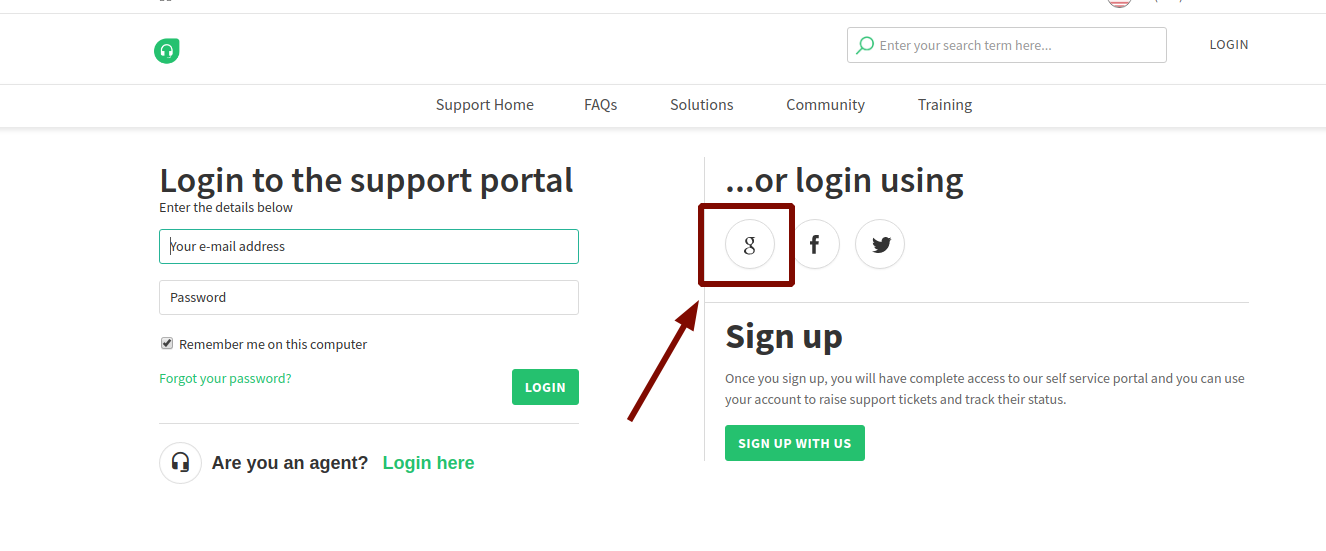
After logging in from our social account as in Figure-1, access to the ticket submission page is provided. It can be seen on this page that the “Sender email address field” can be changed by the end-user. We planned to do tests in two different ways.
First, we will use an email address that does not exist in the company.
Then, we will use a company mailing address. In this context, it is important to prepare beforehand by identifying emails of employees through social networks.
Let’s try to create a new ticket using the mail of [email protected]. When we click the send button, we are redirected to the login screen. At first glance, it is seen that the sender email due to authorization is not the same as the email address we have logged in, and it is redirected to the login screen. Let’s send a ticket again with an email address belonging to the company. Likewise, we were redirected to the login screen.
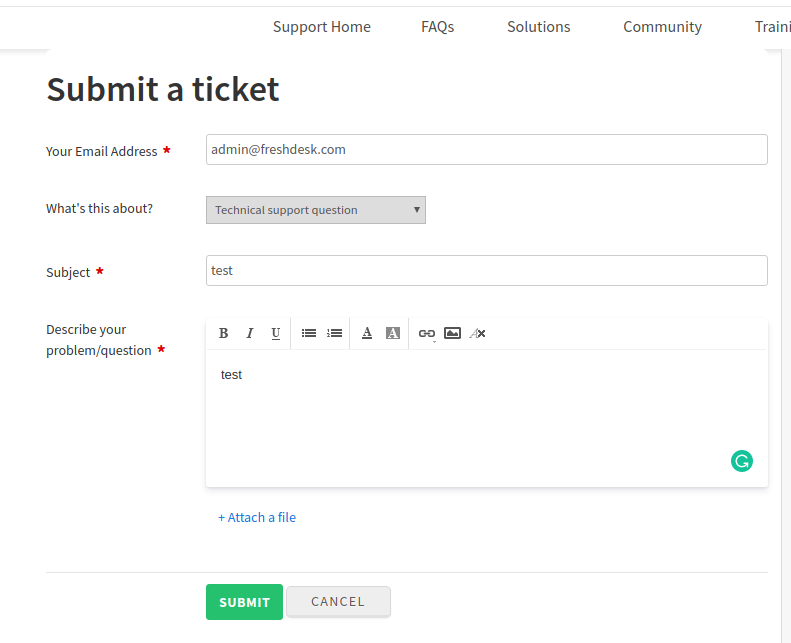
But when we check the admin panel, we saw that we created unauthorized tickets with [email protected] mail and [email protected] mail. At this point, it seems that there is an authorization problem.
When we examined the ticket in the admin panel, the attacker was able to create a more realistic profile with the person’s surname and avatar to imitate “the sender mail address.” By imitating this information, the ticket format seems to be quite misleading, and this can be transformed by attackers into a social engineering vector.
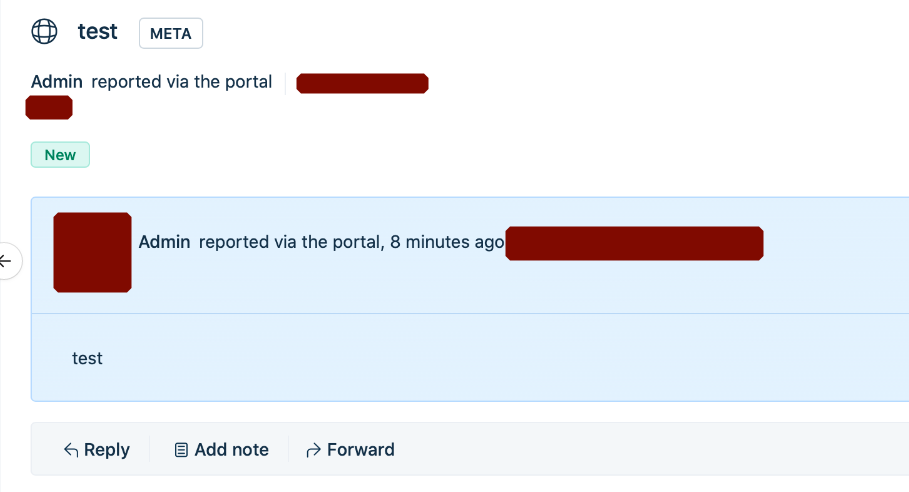
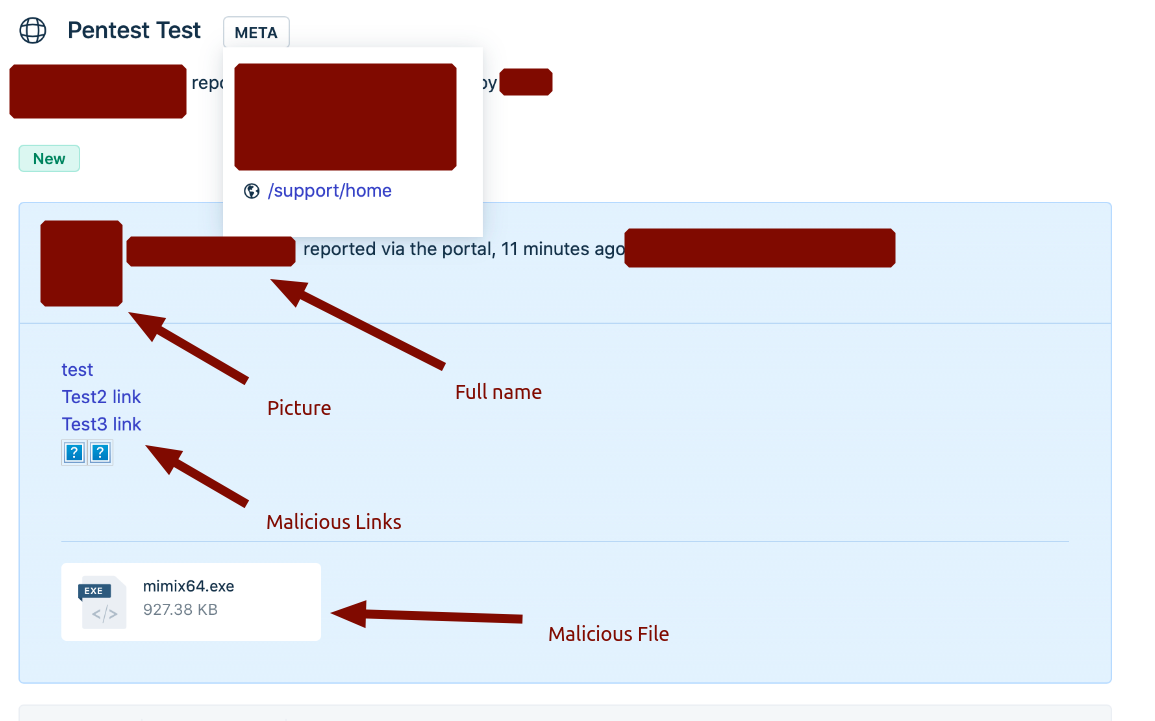
When we consider what we can do from an offensive perspective:
The suggestion offered to Freshdesk: The sender’s email address should not be changed by the end-user.
The suggestion offered to the organizations using Freshdesk: close the social login or/and check the registered users with the confirmation mechanism.
If you close social login completely, a message like below will be displayed:
Sorry! You do not have enough permission to access this page. Please contact your Account administrator.
Special thanks to Barış Akkaya
EOF