Lolbas (Living Off The Land Binaries And Scripts) project was created by Oddvarmoe.
These are files provided by the operating system that are normally used for legitimate purposes but can be abused by malicious actors. Since these files are Microsoft-signed, they are considered to be trusted by organizations.
This project contains very useful features for Red teams. If a file or script has the following features, it can be considered as Lolbas:
Below is a brief analysis of the “certutil, pester, pcwutl.dll, and zipfldr.dll” files from the existing Lolbas techniques.
Additionally, some information has been shared that can support researchers in discovering new Lolbas techniques.
Certutil.exe is a command-line program that is installed as part of Certificate Services. You can use Certutil.exe to dump and display certification authority (CA) configuration information, configure Certificate Services, back up and restore CA components, and verify certificates, key pairs, and certificate chains.
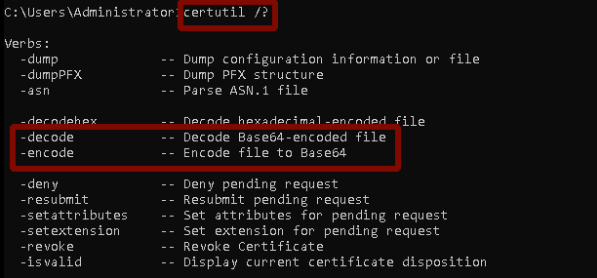
In order to understand how a program works, it is important to understand what parameters can be given as input. In this context, if we check the input parameters of certutil.exe by using “/?,” “/help,” the output can give us preliminary information for further investigation.
In Figure-1, “/?” shows the input parameters of certutil.exe. It is seen that certutil.exe can be used for encoding plain-text data with the base64 algorithm. Attackers use this feature to evade security measures.

Pester is a test framework for PowerShell. It provides a language that allows you to define test cases and the Invoke-Pester cmdlet to execute these tests and report the results.
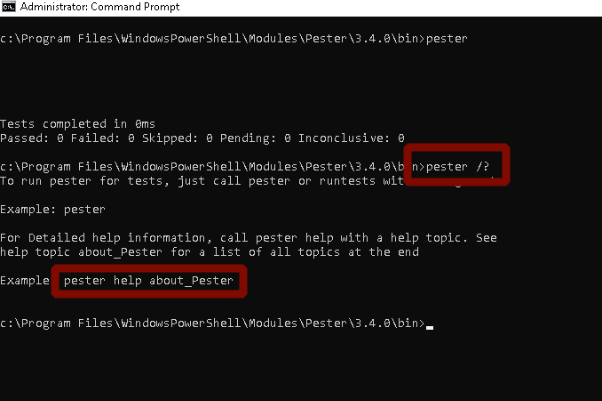
Let’s examine the pester.bat file used by PowerShell. When we get the help menu of the Pester tool, we can see an example usage case in the text (Figure-2). After using the “pester /?” command, we see that it gets help and about_Pester arguments.
In Figure-3 below, when we analyze the source code of the pester.bat file, it can be seen that the %2 variable (related to about_pester) can be controlled by the attacker.
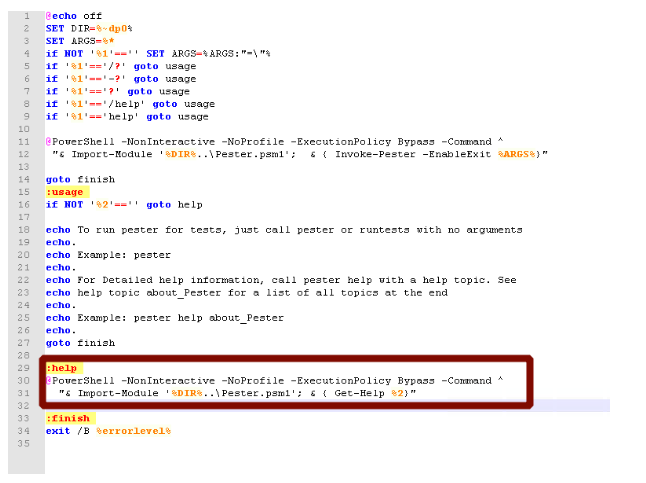
In Code-1, the attacker can inject malicious codes using this part:
pester.bat help "$null; calc"
pester.bat /help "$null; calc"
pester.bat ? "$null; calc"
pester.bat -? "$null; calc"
pester.bat /? "$null; calc"
Let’s analyze some Lolbas DLL files. We are executing “rundll32.exe pcwutl.dll, LaunchApplication calc.exe” command for Pcwutl.dll Html Viewer DLL.
We call the LaunchApplication function from pcwutl.dll by executing Rundll32.exe. The LaunchApplication function executes its parameter and spawns the calc.exe application.
In another DLL example, calc.exe was executed in the same way by calling the RouteTheCall function with the command “rundll32.exe zipfldr.dll, RouteTheCall calc.exe”.
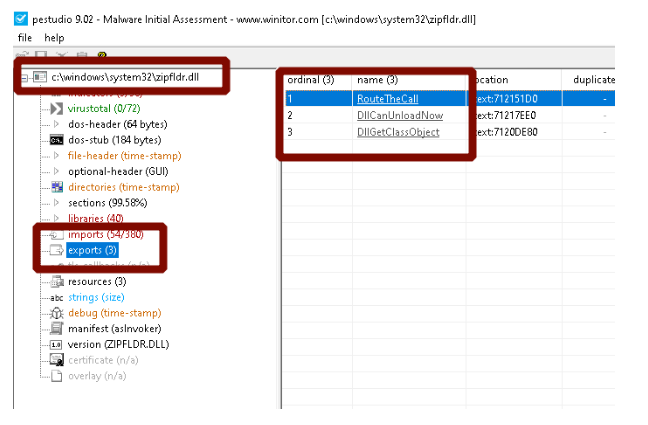
At this point, we can analyze exported functions by System DLLs. In Figure-4, using the Pestudio tool, we can get the relevant function information of the DLL file from the Export menu.
For programs that do not give output when we use the help command, we can apply the following methods:
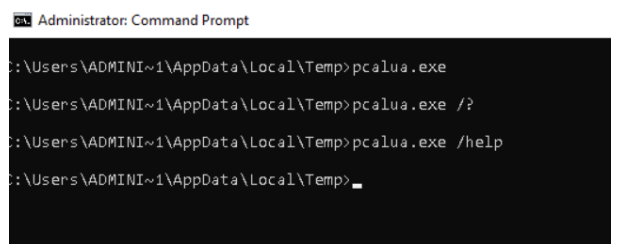
Pcalua.exe is the Program Compatibility Assistant. “The Program Compatibility Assistant is an automatic feature of Windows that runs when it detects an older program has a compatibility problem.”
In Figure-5, we tried to call the help menu of the pcalua.exe file, but the help command does not give any result on a Windows 10 machine. We observed that the pcalua.exe file had the -a parameter with a simple Google search.
We also found some useful information that this program is used in Windows 7 with the -a parameter. When we call “pcalua.exe -a calc.exe” command, we can see that the calculator is executing.
The genuine ie4uinit.exe file is a software component of Internet Explorer by Microsoft Corporation. “Ie4uinit.exe” is a Microsoft utility program having both 32-bit and 64-bit versions.
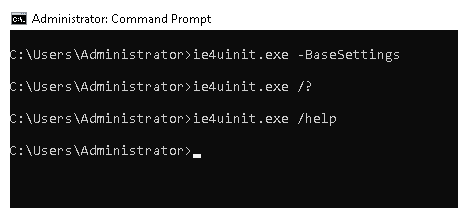
Let’s make another example for a program whose parameter can be used to execute other binaries. See: https://lolbas-project.github.io/lolbas/Binaries/Ie4uinit/
The ie4uinit.exe file in the Lolbas project has the “-BaseSettings” parameter. As seen in Figure-6, we cannot get information about the command with standard help parameters.
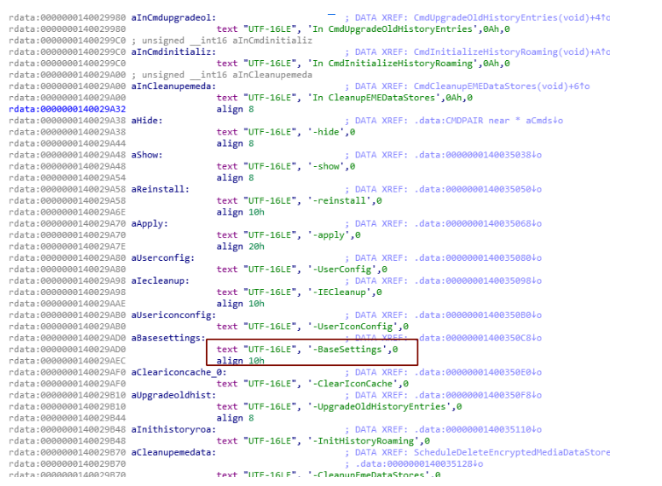
In this case, we can use the “text search” feature of IDA to find other parameters besides the “BaseSettings” parameter. In Figure-7 below, we can see that the EXE file has different parameters such as -hide, -show, etc.
Forfiles is a useful Windows command to select a set of files and then run a command on each of the files. It’s similar to the functionality of the find command on Linux OS.
When we examine the parameter list of the forfiles.exe command, we can see that it can take input parameters like p, m, and c. See: https://lolbas-project.github.io/lolbas/Binaries/Forfiles
forfiles /p c:\windows\system32 /m notepad.exe /c calc.exe
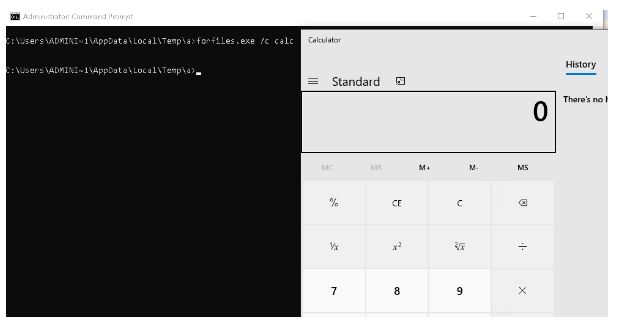
Let’s determine other parameters by reading the help output. In Figure-8, we can see that calc.exe can be executed by using only the “C” parameter.
forfiles.exe /c calc.exe
The Lolbas project includes Microsoft-signed files that exist in the operating system. However, as a different approach, Lolbas can be found in programs belonging to organizations other than Microsoft. In order to conduct research in this context, we analyzed the desktop application called Notion [notion.so] which is a note-taking application used by over 1M people.
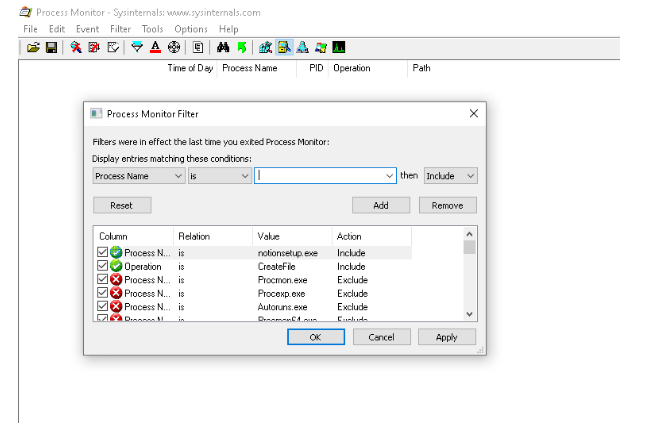
In Figure-9, we will use the Procmon tool in the first step while examining the desktop application. Using this tool, we get an idea about the files created by the Notion desktop application. We list the relevant actions using the filter feature for the installation tool of the Notion application.
In order to display file operations of Notion Installer, we put the name of the installation file of Notion in the “Process name” section of the filter. Then we examine the files/directories created after filtering for CreateFile.
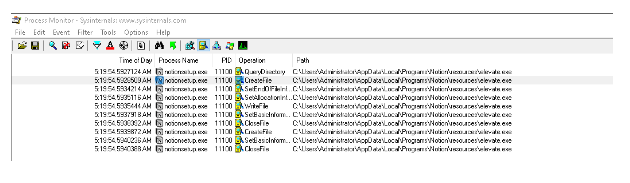
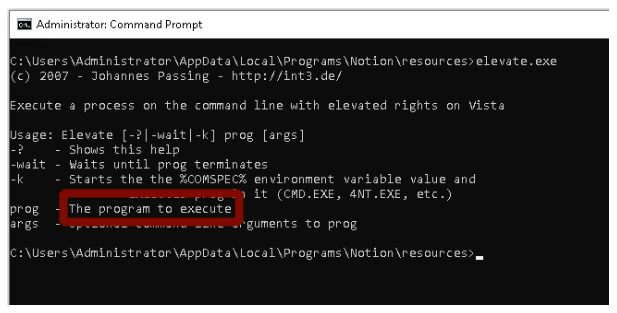
In our review, we observed that the installer created a file called elevate.exe (a tool written by Johannes Passing) in the folder “C:\Users\Administrator\AppData\Local\Programs\Notion\resources”. By sending a command to this program, we can execute calc.
According to Figures 11 and 12, since we can call another program using the elevate program, this program can be considered as Lolbin.
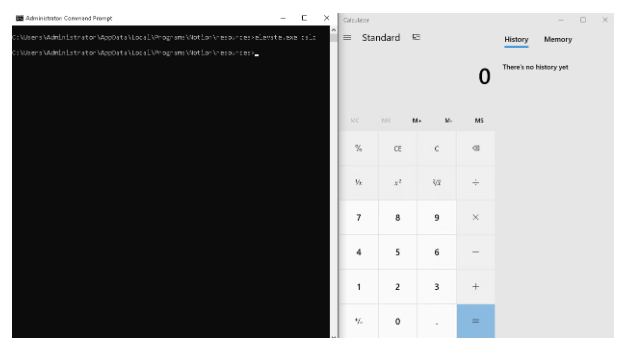
At the same time, when we look at the digital signature of this tool, it is seen that it was signed by the company Notion.
Attacks using LOLBins seem to be increasing. Multiple ways to manipulate these files are constantly shared, so creative defense strategies need to be implemented in the systems.
Thanks to Barış Akkaya